Unveiling the Stealth: How Malware Hides Using Alternate Data Streams

Understanding the intricacies of malware evasion techniques is very important. One such method gaining notoriety is the use of Alternate Data Streams (ADS). In this article, we delve into the covert world of ADS and explore how malware exploits this file system feature to hide from detection.
Alternate Data Streams (ADS)
Alternate Data Streams (ADS) are a little-known feature within the Windows file system. They allow additional data to be associated with a file, often going unnoticed by casual observers. Initially designed for legitimate purposes, ADS has become a tool of choice for malware seeking to evade security measures. We can find many examples from the MITRE list where APTs have used ADS to hide their payloads.
Creating ADS
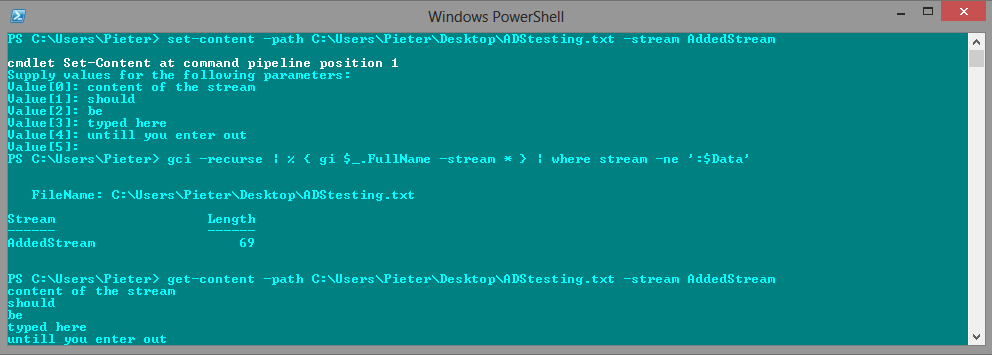
First we can add random text to a text file.

Next, we create an Alternate Data Stream (ADS) file using the command below and link it to the original file created in the initial step.
cmd '/c echo "This is a hidden text" > cleartext.txt:hidden.txt'Upon reviewing the screenshot below, it becomes evident that the ADS file ("hidden.txt") is not visible using the PowerShell command Get-ChildItem. However, utilizing the command prompt with the dir \R command reveals all ADS files associated with "cleartext.txt."

Inspecting the file explorer, we find that the "hidden.txt" file remains invisible.

Malware and Alternate Data Streams
Below are some ways malwares use ADS to hide from plain sight:
- ADS in Conficker Worm:
The Conficker worm, a notorious malware that emerged in the late 2000s, was known for using ADS to hide its malicious payload. It crea ted hidden streams within the Windows file system, making it challenging for traditional antivirus solutions to detect and remove the malware. - Steganography-Based Malware:
Some malware employs steganography techniques to hide malicious code within images or other seemingly innocuous files. The use of ADS allows these threats to store additional data alongside the legitimate file, making it harder for security tools to identify the hidden payload. - Fileless Malware Techniques:
Certain fileless malware strains leverage ADS as part of their evasion tactics. These threats operate in memory without leaving a traditional file footprint, but they may use ADS to store and execute malicious code, leaving minimal traces on disk. - Banking Trojans and ADS:
Banking trojans, which aim to steal sensitive financial information, often use ADS to conceal their presence. By hiding in alternate streams, these trojans can maintain persistence on infected systems and avoid detection by traditional signature-based antivirus solutions.
Analysis Techniques
There are several native tools available for detecting and analyzing Alternate Data Streams:
- Echo and More.
- Sysinternals Suite utilities like
StreamsandProcmon. - The /R option of the Dir command.
- PowerShell, which includes six cmdlets (
Add-Content,Clear-Content,Get-Content,Set-Content,Start-ProcessandOut-File) to directly manipulate content for ADS.
Using Command Prompt and More
To identify any Alternate Data Stream (ADS) files, the command dir /R can be utilized.

Once the ADS files have been located, the more command can be used to read their contents.

Using PowerShell and Stream
With PowerShell, the Sysinternals Stream tool proves effective in locating Alternate Data Stream (ADS) files.

Once the name of the stream is identified, the following PowerShell command can be used to read the content of the "hidden.txt" file.
Get-Content .\cleartext.txt -Stream hidden.txt
Mitigation Strategies
The challenge with Alternate Data Streams (ADSs) lies in their inherent invisibility within NTFS Windows systems, creating a significant security hurdle. Detecting these streams demands extra effort due to their seamless integration into the file system. Despite our understanding of common malicious uses of ADSs, their presence remains a security vulnerability, exploiting a blind spot.
The real danger of ADSs becomes apparent when they go unnoticed and unaccounted for, introducing all the associated issues and risks of the standard file system. Without deliberately deviating from conventional file-review procedures in security operations center, identifying silently lurking ADSs housing malicious scripts becomes a nearly impossible task. To address the potential widespread abuse of ADSs across the network, it is crucial to update standard security-operation practices with customized diagnostic measures and countermeasures specifically designed to prevent the presence of rogue, unwanted ADSs.
Here are some mitigation strategies:
- File System Auditing: Monitor changes to the file system, focusing on the creation and deletion of ADSs.
- Hash-based Detection: Monitor file integrity by comparing hash values to detect changes, including the addition of ADSs.
- Regular File System Scans: Generate an alert if a file with an unauthorized ADS is discovered during a routine file system scan.
Detection Rule:
This Sigma rule detects the creation of Alternate Data Streams (ADS) and related execution on Windows. The rule identifies the creation of ADS using EventID 4663 and the presence of specific system utilities (PowerShell, WMIC, rundll32, wscript/cscript) in the execution path, signaling potential malicious activity
involving Alternate Data Streams.
title: Detect ADS Creation and Execution
id: denwp-0001
description: Detects the creation of Alternate Data Streams (ADS) and related execution on Windows.
author: denwp
status: experimental
references:
- https://example.com/sigma-rule-doc
logsource:
category: security
product: windows
definition: 'EventID == 4663 OR event_id == 1'
detection:
selection:
- EventID: 4663
Object_Type: File
Object_Name: '*\\*:*:$DATA'
AccessMask: 0x2 # FILE_WRITE_DATA
- Image:
- "C:\\Windows\\powershell.exe"
- "C:\\Windows\\wmic.exe"
- "C:\\Windows\\rundll32.exe"
- "C:\\Windows\\wscript.exe"
- "C:\\Windows\\cscript.exe"
condition: selection
powershell_ads_execution: >-
filter processes where (
event_id = 1 AND
exe = "C:\\Windows\\powershell.exe" AND
command_line = "Invoke-CimMethod\s+-ClassName\s+Win32_Process\s+-MethodName\s+Create.\b(\w+(.\w+)?):(\w+(.\w+)?)|-ep bypass\s+-\s+<.\b(\w+(.\w+)?):(\w+(.\w+)?)|-command.Get-Content.-Stream.Set-Content.start-process .(\w+(.\w+)?)"
)
wmic_ads_execution: >-
filter processes where (
event_id = 1 AND
exe = "C:\\Windows\\wmic.exe" AND
command_line = "process call create.\"(\w+(.\w+)?):(\w+(.\w+)?)"
)
rundll32_ads_execution: >-
filter processes where (
event_id = 1 AND
exe = "C:\\Windows\\rundll32.exe" AND
command_line = "\"?(\w+(.\w+)?):(\w+(.\w+)?)?\"?,\w+\|(advpack.dll\|ieadvpack.dll),RegisterOCX\s+(\w+.\w+):(\w+(.\w+)?)\|(shdocvw.dll\|ieframe.dll),OpenURL.(\w+.\w+):(\w+(.\w+)?)"
)
wscript_cscript_ads_execution: >-
filter processes where (
event_id = 1 AND
(exe = "C:\\Windows\\wscript.exe" OR exe = "C:\\Windows\\cscript.exe") AND
command_line = "(?<!\/)\b\w+(.\w+)?:\w+(.\w+)?$"
)
falsepositives:
- Legitimate ADS creation and execution activities.
level: high
Reference: